Key Takeaways
- CMMC will be a phased in approach with new contracts starting Q4 2020 through 2026
- Subcontractors will be required to meet CMMC Maturity Level requirements
- CMMC Maturity Level 1 and 2 are required to work with FCI (Federal Contracting Information)
- CMMC Maturity Level 3 and above are required to work with CUI (Controlled Unclassified Information)
- With any new program, expect changes to occur periodically

An Overview of the CMMC
The Department of Defense (DoD) has put together the Cybersecurity Maturity Model Certification (CMMC) in response to the increase of malicious cyber attacks. It was estimated that malicious cyber activity cost the U.S. economy between $57 billion and $109 billion in 2016. These numbers are expected to increase in the coming years.
In order to combat this, the CMMC has various maturity levels that range from “Basic” to “Advanced” Cybersecurity hygiene for organizations to achieve. This way, Controlled Unclassified Information (CUI) found in the Defense Industrial Base (DIB) systems and networks should remain sufficiently protected.
What was the Reasoning for the CMMC?
First, the DoD implemented requirements for safeguarding Covered Defense Information (CDI) and cyber incident reporting. In October 2016, through Defense Federal Regulation Supplement (DFARS) 252.204-7012, the documents were released.
DoD Contractors were charged with their own security controls within contractor systems. The reasoning was to ensure that CDI (“covered defense information”) remained confidential.
The DFARS’s required security controls are defined within the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations.
Then, in March 2019, the Office of the Undersecretary of Defense for Acquisition and Sustainment (OUSD (A&S)) started creating the CMMC. The CMMC v1.0 was finalized on January 31st of this year.
Throughout the rest of this article will be more intricate details about the CMMC.
The CMMC’s Immediate Impact
Any DoD contractors taken off-guard by the CMMC can breathe easy, knowing that not everyone is expected to follow the mandates right away.
Instead, the various rules and regulations were phased in during September for specific DoD contractors.
Once the CMMC is operating at full capacity, any organizations working alongside the DoD at all levels must adhere to the mandated standards.
More specifically, the DoD’s prime contractors and subcontractors must satisfy 1/5 of CMMC’s trust levels. These entities must prove sufficient cybersecurity implementation via completing independent validation activities.
Being awarded or allowed to continue with a DoD contract will hinge upon complying with CMMC’s rules.
Provided a contracted organization fails to meet the CMMC requirements, they can’t receive or share DoD information involving programs and projects.
Furthermore, when it’s time to renew contracts, contractors are only eligible if they’re compliant with the CMMC’s expectations.
A checklist was released this past January, giving contractors the necessary information to comply with the CMMC framework. Plus, having these items listed should aid tremendously in planning and implementing security maturity tasks.
Halfway through this year, the CMMC became a component of Requests for Information (RFIs). It should be included in Requests for Proposal (RFPs) by late 2020.
Sections L & M of RFPs will contain the necessary CMMC compliance level. Thus, cybersecurity will be an “allowable cost” within DoD contracts.
Keep in mind that not all contracts will require CMMC compliance levels. The goal is to eventually have CMMC compliance requires in all contracts by 2026.
Breaking Down the CMMC’s Compliance Framework
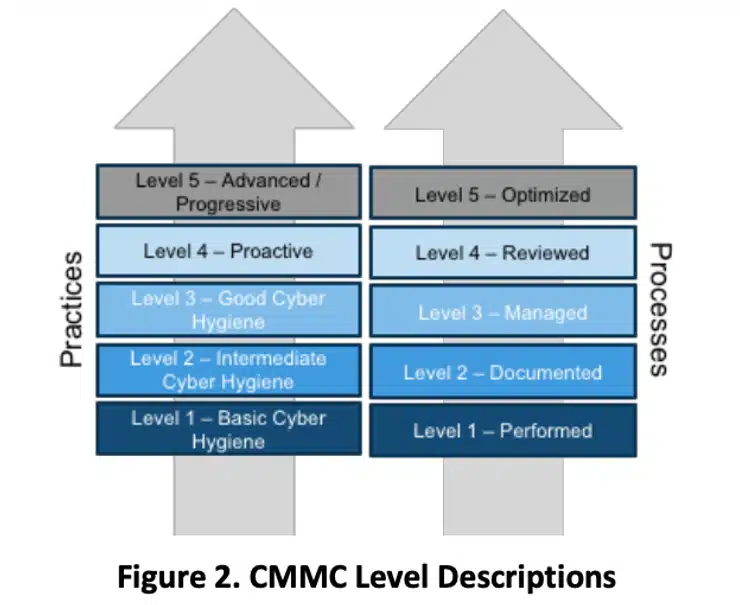
source:securityboulevard.com
Below are the 5 levels involved in the CMMC’s framework:
1. Basic Cyber Hygiene:
- Any small companies incorporating common practices must incorporate base-level cybersecurity standards.
- This necessitates a few performed practices, even if they’re ad hoc and not pre-planned.
- At the “Basic Cyber Hygiene” level, 35 security controls must be implemented and fully functional.
2. Intermediate Cyber Hygiene:
- This step incorporates universally accepted cybersecurity best practices.
- The tracking and documentation of practices are required at this level.
- Multi-factor authentication will be needed to access CUI data.
- Compared to level 1, “Intermediate Hygiene” includes an additional 115 security controls.
3. Good Cyber Hygiene:
- This level is a significant ramp-up in CMMC requirements that includes
- 100% NIST SP 800-171 Rev. 1 controls coverage.
- Practices that eclipse the CUI’s protective scope.
- For “Good Cyber Hygiene,” it’s expected that processes are maintained and followed.
- There must also be comprehensive cyber-asset knowledge.
- Compared to levels 1 and 2, “Good Cyber Hygiene” includes an additional 91 security controls.
4. Proactive:
- The “Proactive” level adds advanced and sophisticated cybersecurity practices to its list of expectations.
- Proactive processes will be reviewed, adequately resourced, and regularly improved across the enterprise:
- All of these procedures will be performed periodically.
- It’s also required for defensive responses to operate at machine speed.
- Cyber assets must be comprehensively learned and understood.
- Compared to the first 3 levels, “Proactive” includes an additional 95 controls.
5. Advanced or Progressive:
- Of course, this level possesses the most multi-dimensional and advanced cybersecurity practices.
- The “Advanced/Progressive” level requires continuous cross-enterprise improvements.
- All defensive responses must perform at machine speed.
- Compared to the other 4 levels, “Advanced/Progressive” includes an additional 34 controls.
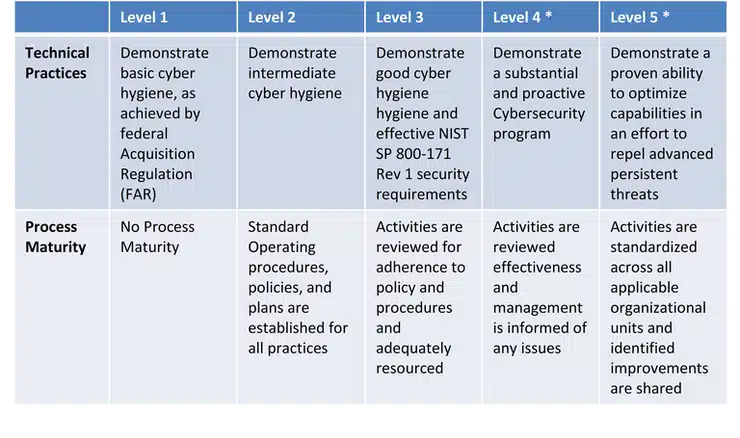
source:securityboulevard.com
The Need for Independent Assessments
A periodic, independent assessment of DoD contractors’ CMMC implementation of the security controls protecting CUI data is required.
The entity charged with overseeing this process is the CMMC 3rd Party Assessment Organization (C3PAO). It will replace the NIST 800-171 compliance – which involves an internal entity that performs self-attestation.
Recently, 10 DoD contractors’ servicing contracts were audited. These deals exceeded $1 million in value.
There was one finding that stood out about these audits:
Self-attested compliance methods incorporated via NIST SP 800-171 proved insufficient when implementing base-level cybersecurity controls.
It’s then worth asking why these deficiencies existed with the NIST SP 800-171 framework?
According to a more high-level analysis, it was due to the NIST SP 800-171’s failure to consider the implemented controls’ strength or maturity. Also, there were deficiencies involving control execution.
The Great Differentiator: Process Institutionalization
Here are the various facets involved in process institutionalization:
- Policies
- Plans
- Processes
- Procedures
These 4 pivotal p-words are integral to CUI environment management – and it’ll differentiate the CMMC from its predecessors. It’ll ensure the successful and sustainable implementation of these newly required practices.
Also, asset management, cybersecurity governance, recovery, and situational awareness will all play critical roles. These 4 additional controls are yet to be covered under NIST 800-171 – but they are included in the CMMC Domains.
Professionals and Organization Types Involved with CMMC
Professional Roles in the CMMC
First, here are the professional roles involved with the CMMC:
Registered Practitioners:
- This role includes the authorization of CMMC-AB branding in the course of providing non-certified services to OSCs.
Certified Assessors:
- These individuals receive training and testing, earning the ability to certifiably assess and consult with OSCs.
Licensed Instructor:
- People with this job earn certifications allowing them to teach assessor applicants about intricacies involved in their CMMC assessment practices.
CMMC-AB Staff:
- In January 2020, the CMMC-AB Staff was formed to further bolster this ground-up organization.
Professional Organizations in the CMMC
Now, let’s look at the types of organizational entities involved in the CMMC:
Registered Provider Organization:
- These entities comprise themselves with Registered Practitioners, providing these professionals with the required basic CMMC-AB training.
- Such entities also include teachings that enforce the CMMC-AB Code of Professional Conduct.
C3PAO:
- These have already been discussed, but Certified Third-Party Assessment Organizations are Certified Assessors’ stomping grounds.
- The C3PAO ensures that Assessors stick to the CMMC-AB Code of Professional Conduct.
- Furthermore, the C3PAO helps schedule assessments, review, and submit completed assessments for certification by the CMMC-AB.
Licensed Training Provider (LTPS):
- Universities, community colleges, training Certified Professionals, and Certified Assessors are all training provider list.
Licensed Partner Publisher:
- These entities are responsible for bringing forth the materials for LTPs.
Any business, big or small, working with the DoD would benefit from knowing the ins and outs of the CMMC. Grasping these structural nuances could pay dividends, allowing relevant contractors to be more attuned to compliance measures.
Additional CMMC Talking Points
Is the CMMC Good for the Industry? The answer to this question is a resounding YES.
This monumental shift will prove beneficial in a widespread manner because it’ll provide a warfighting advantage and preserve intellectual property.
Beyond that, CMMC promotes meaningful cybersecurity investments by creating a new baseline expectation. Therefore, the playing field will be leveled for those who’ve already been following best practices.
For many businesses, this is yet another hurdle to get through, but the ROI will be realized from the reduction of damage due to cyber crimes.
What Maturity Level Should Organizations Strive For ?
Any organization charged with storing or creating government data will possess – at a minimum – Federal Contract Information (FCI). Furthermore, these contractors will contain CUI.
Entities responsible for storing, processing, or transiting CUI should aim for Level 3 (Good Cyber Hygiene) certification.
Holding export controlled (ITAR) data should know that it’s viewed as CUI. Therefore, it falls under the Level-3 umbrella on top of additional ITAR-based rules.
Lastly, it’s worth bringing up that CMMC guidelines for levels 4 and 5 have yet to be fully formed.
There’s No Magic Solution
Satisfying the CMMC’s regulated requirements isn’t a matter of snapping one’s fingers and watching it all come together.
Instead, compliance involves integrating a steady stream of new solutions.
Here’s a list of the necessary solutions for eliminating cyber-vulnerabilities:
- Compliant platforms
- Encrypted assets
- Data back-ups
- Monitoring
- Management
These solutions must all work in unison to bolster cybersecurity and meet CMMC standards.
Do You Work with Sensitive Data? Then it’s Time to Bolster Your Cybersecurity.
It would be unfortunate for businesses to fall behind on best practices and face sanctions from the relevant governing bodies enforcing CMMC regulations.
Sure, at first, there will be patience practiced by those in charge.
Eventually, however, it’ll be expected that everyone’s caught up. Now is the time for organizations to bolster their cybersecurity practices. In fact, even businesses not involved in DoD contracting could benefit from being CMMC compliant. It’s expected that cybercrimes will increase by 600% over the next few years. Now is the time to evaluate current cybersecurity policies and processes to ensure your organization is properly safeguarding information from potential attacks.
Have more questions regarding the CMMC? Reach out today and know more about cybersecurity services.






