
Bridging the Gap: What HR Needs from IT and What IT Needs from HR
Introduction The digital transformation of businesses has blurred the traditional boundaries between HR and IT. Human Resources (HR) departments increasingly
The Department of Defense developed the Cybersecurity Maturity Model Certification (CMMC) program in 2020. A year later, they rolled out CMMC 2.0 with the intention of enhancing the protection of sensitive information, especially Controlled Unclassified Information (CUI), within the Defense Industrial Base (DIB).

We manage all areas of CMMC certification as your outsourced cybersecurity department so you don’t have to.
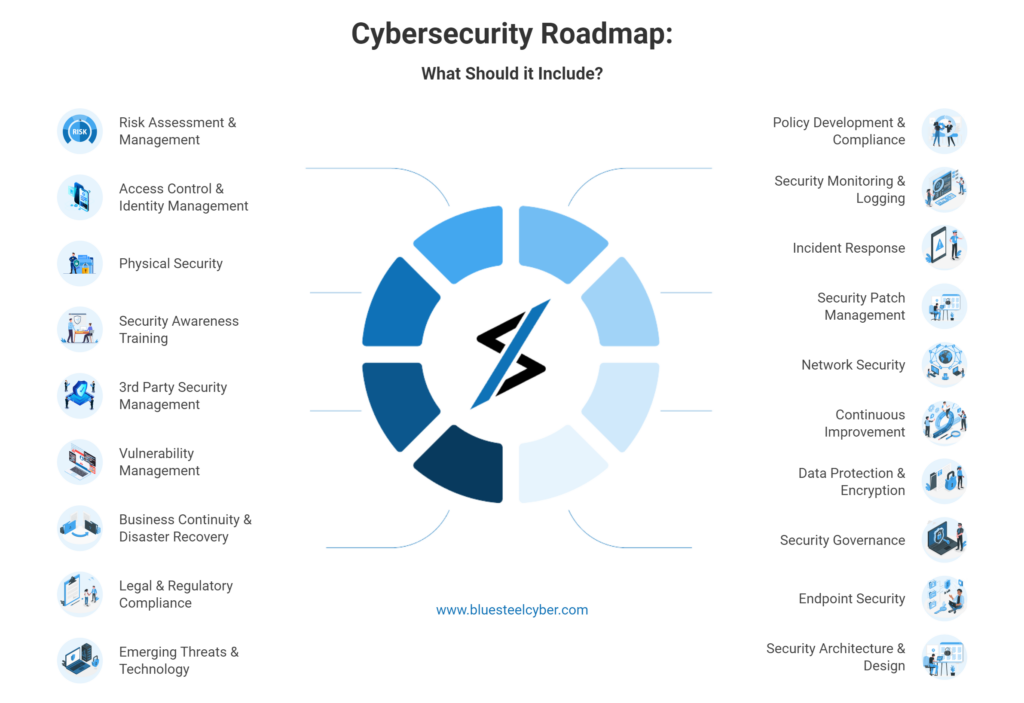
Our CMMC Security Program includes everything you need to meet all levels of CMMC criteria items, but also NIST-800-171 controls. This includes the following:
Explained below are some of the most critical aspects of the CMMC and CMMC requirements that every organization that deals with CUI should be aware of.
How do the CMMC 1.0 and 2.0 differ? Some of the key differences between the two versions of the certification are explained below:

The CMMC 1.0 model had five certification levels. However, the CMMC 2.0 model has just three. They are as follows:

This level is necessary for DoD contractors and subcontractors that handle CUI and FCI (Federal Contact Information).

This level requires the implementation of advanced practices, including system hardening and data recovery. It is designed to protect CUI's confidentiality, integrity, and availability from advanced persistent threats.

This level requires organizations to implement more advanced cybersecurity practices, including access control, media protection, and incident response. It aligns with the National Institute of Standards & Technology SP 800-171 (NIST 800-171) and requires triennial third-party assessments by a CMMC Third-Party Assessor Organization (C3PAO).
The number of security domains included in the CMMC 2.0 model is much higher than the CMMC 1.0 model.
These additional domains are more closely related to day-to-day operations. They include various topics, including the following:




These new domains provide a more holistic view of contractors’ operations and offer more assurance of their asset security.
The CMMC 2.0 model requires the use of C3PAO for both Level 2 and Level 3. C3PAOs are responsible for assessing and certifying companies in the DIB supply chain and ensuring they have met the standard CMMC cybersecurity requirements. They also conduct evaluations and issue certificates of adherence.
In addition to the three levels of CMMC 2.0, 17 Core Security Domains represent the specific security practices to which organizations must conform when working with CUI.
The 17 domains are listed below:

Restrict access to CUI

Keep track of and report who accesses CUI

Maintain the integrity of information systems

Detect and respond promptly to security incidents

Safeguard CUI that is stored on removable media

Ensure proper physical security of equipment and facilities

Identify and address all vulnerabilities to mitigate risk

Recognize and ensure understanding of changes and anomalies

System and Information Integrity (SI): Protect information and information systems from threats

Understand your CUI

Develop and reinforce proper CUI-handling protocols

Ensure only authorized personnel can access CUI

Ensure information systems run optimally

Vet and protect the employees who handle CUI

Respond to and rebound from security events

Evaluate security requirements and make a plan to meet the requirements

Implement controls to identify and repel potential threats
Any individual in the Department of Defense supply chain. The list of those who must comply with the CMMC 2.0 guidelines includes contractors who exclusively engage with the Department of Defense, as well as any and all subcontractors.
The following are some examples of individuals that must be compliant:

Department of Defense prime contractors

Department of Defense subcontractors
Suppliers at all tiers in the Defense Industrial Base (DIB)

Department of Defense small businesses suppliers

Commercial suppliers that process, handle, or store CUI

Foreign suppliers

Team members of Department of Defense contractors that handle CUI (e.g., IT-managed service providers)
The specific level of CMMC compliance contractors and subcontractors must meet is based on the type of CUI and FCI that they handle and exchange.
Organizations have until October 2025 to become compliant with the newest version of the CMMC. That might seem like a long way away, but time moves more quickly than most of us think. The sooner you get started, the better off you and your team will be.
The following are some specific advantages that come with beginning your compliance journey now:

Soon, the DoD will require contractors and subcontractors to be CMMC-certified for new contracts. If you’ve already taken steps to become CMMC-certified, you’ll stand out from your competitors and be more likely to be selected.

Achieving compliance now proves you take CMMC seriously and are unlikely to cause any compliance problems for your affiliates.

CMMC offers a detailed outline for how you can secure information systems and data. Implementing these controls allows you to strengthen your cybersecurity strategy and reduce the risks your organization faces.

CMMC can reduce your organization’s liability in the event of a data breach or any other cybersecurity incident. If you’re compliant, you can prove that you did everything correctly and are not to blame.
You understand the benefits of being CMMC-compliant, but do you know how to get your organization certified? Here are the essential steps to start taking today:

The first step is determining your CMMC level (1, 2, or 3). Here’s a quick breakdown of who falls under which category:

Department of Defense contractors and subcontractors that handle FCI, or “Information not intended for public release [that] is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government.”

Department of Defense contractors and subcontractors that handle the same type of CUI must meet level 2 compliance. If only select information flows down to the subcontractor, a lower CMMC level may apply.

Level 3 applies to Department of Defense contractors and subcontractors that handle CUI for DoD programs with the highest priority.

The next step is to conduct a self-assessment to get a better idea of how your organization is doing and where you need to improve when it comes to cybersecurity. Your assessment should include a thorough review of your cybersecurity maturity, including policies and procedures, access control, network security, and incident response strategies and capabilities.

The CMMC was developed from existing frameworks, and because of this, there is significant overlap. Some frameworks and certifications that can help you achieve CMMC certification include the following:
By ensuring compliance with these frameworks and certifications, you can improve your overall cybersecurity strategy and ensure compliance with CMMC requirements.

If your self-assessment revealed weaknesses in specific areas, create a plan of action to focus on those and ensure they’re up to par. Establish distinct milestones so you can measure progress and ensure you haven’t missed any critical steps.

CMMC-compliant organizations must create a system security plan (SSP).
This plan should include details about each system in the IT environment that stores or transmits controlled unclassified information (CUI). For example, it should outline the flow of information between systems, along with company regulations, network diagrams, administrative duties, and staff security requirements.
Remember that the SSP is a living document. You should update it whenever you make significant changes to your security profile/procedures.

A CMMC Third Party Assessor Organization (C3PAO) has been authorized to conduct CMMC assessments. They will assess your organization’s compliance with the CMMC guidelines.
When looking for an authorized C3PAO, make sure they have experience in your industry and are appropriately accredited through the Cyber AB (the official CMMC accreditation body). You should also ask for references and seek feedback from previous clients.
Once you’ve chosen a C3PAO, you will work closely with them. They will provide guidance and help you understand the essential steps you must take to achieve and maintain compliance.
CMMC compliance can give your organization a competitive advantage, enhance your cybersecurity strategy, and reduce your liability.
If you haven’t updated your cybersecurity protocols to be compliant with CMMC 2.0, now is the perfect time to get started. Follow the steps outlined above, and if you need more guidance or support, our team at Bluesteel Cybersecurity is ready to assist.
Contact us today for more information on CMMC certification training and compliance.

For any organization that deals with electronic protected health information, compliance with HIPAA and the HITECH Act is critical. Making sure you are compliant, especially with the latest updates, can be tricky, though.
Follow the guidelines shared here to begin ensuring compliance. If you need more assistance, though, reach out to our team at Bluesteel Cybersecurity.
We offer compliance preparation services to help you feel confident that you’ve checked every box and done everything you can to protect your business and your customers/clients.

Introduction The digital transformation of businesses has blurred the traditional boundaries between HR and IT. Human Resources (HR) departments increasingly

Introduction In today’s fast-paced software development landscape, third-party code plays a crucial role in accelerating innovation and delivering value to

SOC 2 Compliance for CEOs: What You Need to Know For CEOs of SaaS companies and service-based tech businesses, data
Reach us Monday through Friday
8am – 6pm