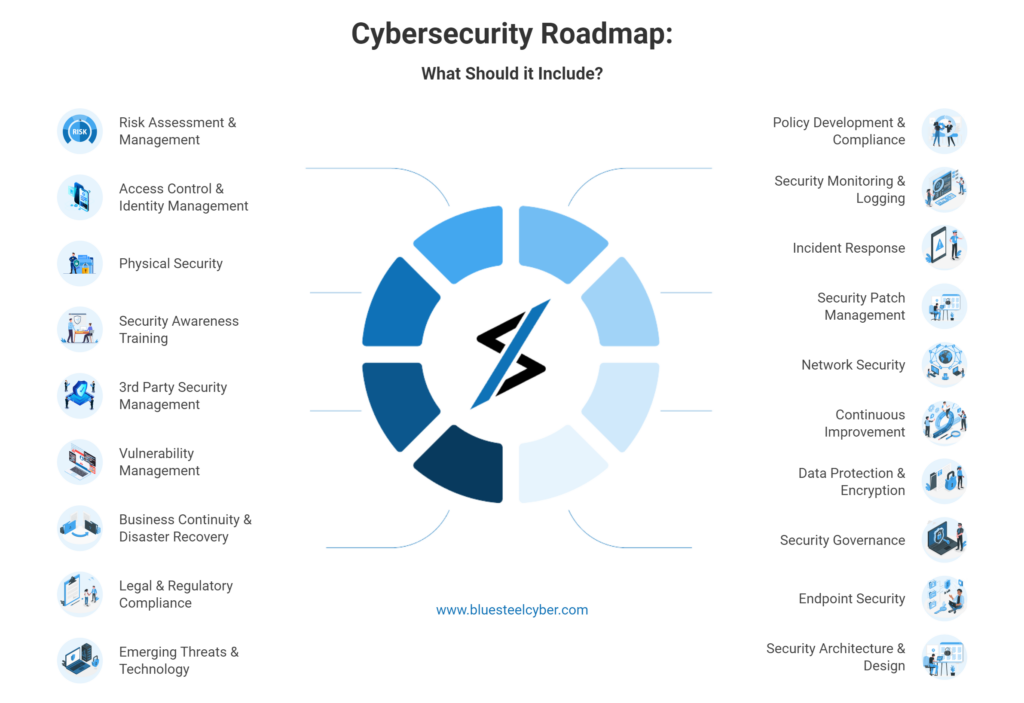
Strengthening OT Security: Key Challenges and Essential Controls for Today’s Industrial Environments
Introduction In critical infrastructure sectors like energy, manufacturing, and transportation, Operational Technology (OT) security is essential for protecting industrial control