
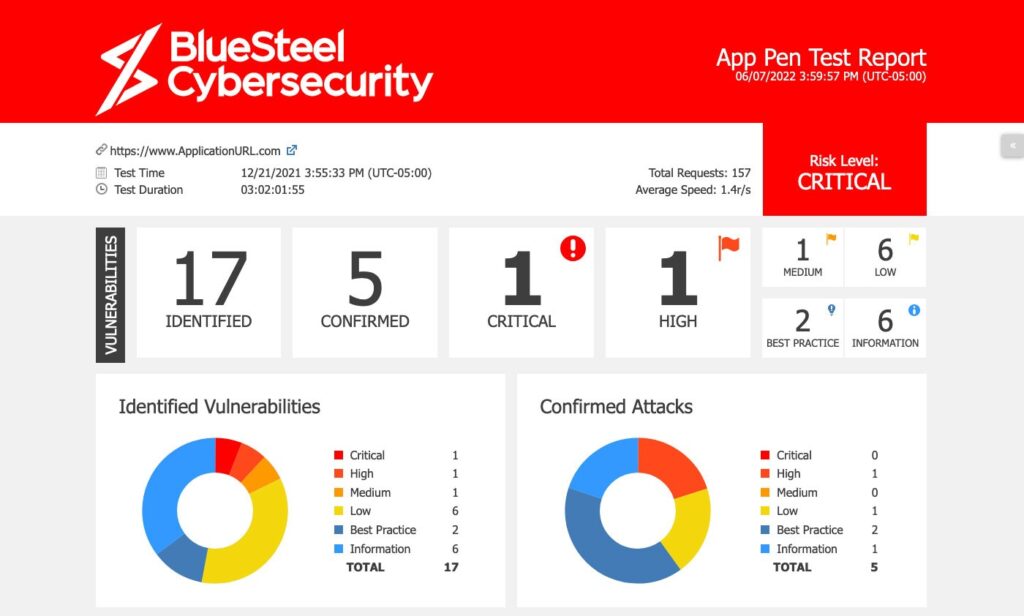
In today’s digital landscape, the security of your organization’s infrastructure and sensitive data is critical. Cyber threats evolve quickly, making it critical for firms to keep ahead of possible hazards. Penetration testing, often known as ethical hacking, is a proactive method of finding and resolving vulnerabilities before they are exploited by bad actors.
Starting at $5,000, our Penetration Testing Services help organizations identify network and software application vulnerabilities quickly.
A penetration test, sometimes known as a “pen test,” is a simulated cyberattack on end user devices, on premise networks, cloud networks, or applications conducted by security specialists. A penetration test aims to detect weaknesses in the target system’s security posture before hostile attackers can exploit them.
Testing scope can range in breadth and complexity, from evaluating specific applications or components to conducting thorough audits of an organization’s network infrastructure.
Penetration testing assists organizations in identifying and addressing security vulnerabilities, the opportunity to address these vulnerabilities, and providing a Penetration Testing Report to validate your organization’s security posture to customers.

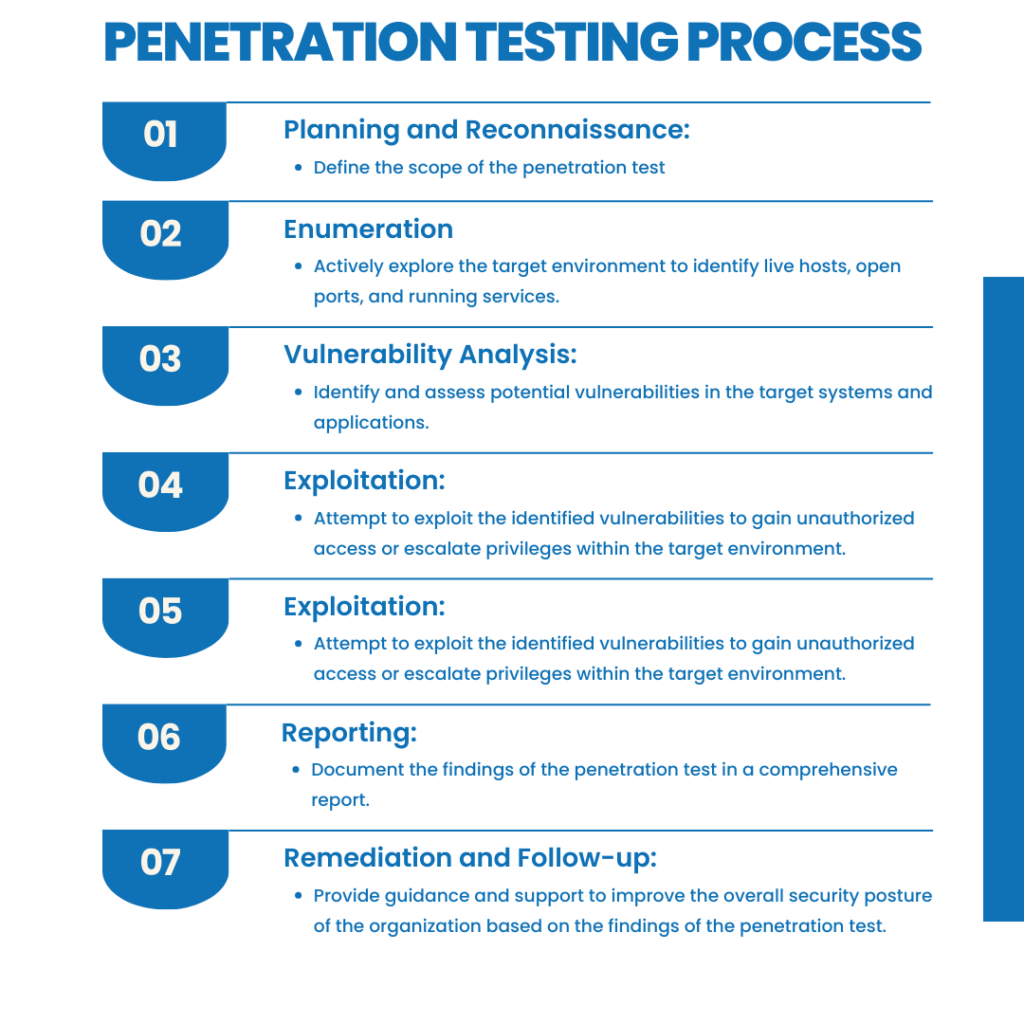
There are many types of Penetration Testing. Here are the most common:
Application or Software Penetration Testing: This focuses on identifying vulnerabilities in applications such as online banking systems, e-commerce websites, SaaS products, and web portals. Common vulnerabilities include SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms.
Mobile Application Penetration Testing: With the proliferation of mobile devices and applications, testing the security of mobile apps is essential. This involves identifying vulnerabilities that could be exploited to compromise the confidentiality, integrity, or availability of sensitive data stored or processed by mobile applications.
Black Box Testing: In black box testing, the tester has no prior knowledge of the system being tested. This simulates the perspective of an external attacker and helps identify vulnerabilities that may not be obvious to insiders.
White Box Testing: In white box testing, the tester has full knowledge of the system’s internals, including source code, architecture, and configurations. This allows for a more comprehensive assessment of security vulnerabilities.


Penetration testing, also known as pen testing or ethical hacking, offers several benefits to organizations:
The cost of a penetration test can vary significantly based on several factors, including the scope of the test, the complexity of the systems being tested, the depth of the assessment, the experience and reputation of the security firm or individual conducting the test, and the geographic location. Here are some general considerations that can influence the cost:
It’s essential to obtain quotes from several reputable security firms or professionals and carefully evaluate their proposals to ensure they meet your specific needs and budget constraints. Additionally, consider the long-term value of investing in thorough security testing to protect your organization from potential data breaches and cyberattacks.


Reach us Monday through Friday
8am – 6pm