Penetration Testing Services



In today’s digital landscape, the security of your organization’s infrastructure and sensitive data is critical. Cyber threats evolve quickly, making it critical for firms to keep ahead of possible hazards. Penetration testing, often known as ethical hacking, is a proactive method of finding and resolving vulnerabilities before they are exploited by bad actors.
Starting at $5,000, our Penetration Testing Services help organizations identify network and software application vulnerabilities quickly.
Quick Hassle Free Quote

What is a Penetration Test
A penetration test, sometimes known as a “pen test,” is a simulated cyberattack on end user devices, on premise networks, cloud networks, or applications conducted by security specialists. A penetration test aims to detect weaknesses in the target system’s security posture before hostile attackers can exploit them.
Testing scope can range in breadth and complexity, from evaluating specific applications or components to conducting thorough audits of an organization’s network infrastructure.
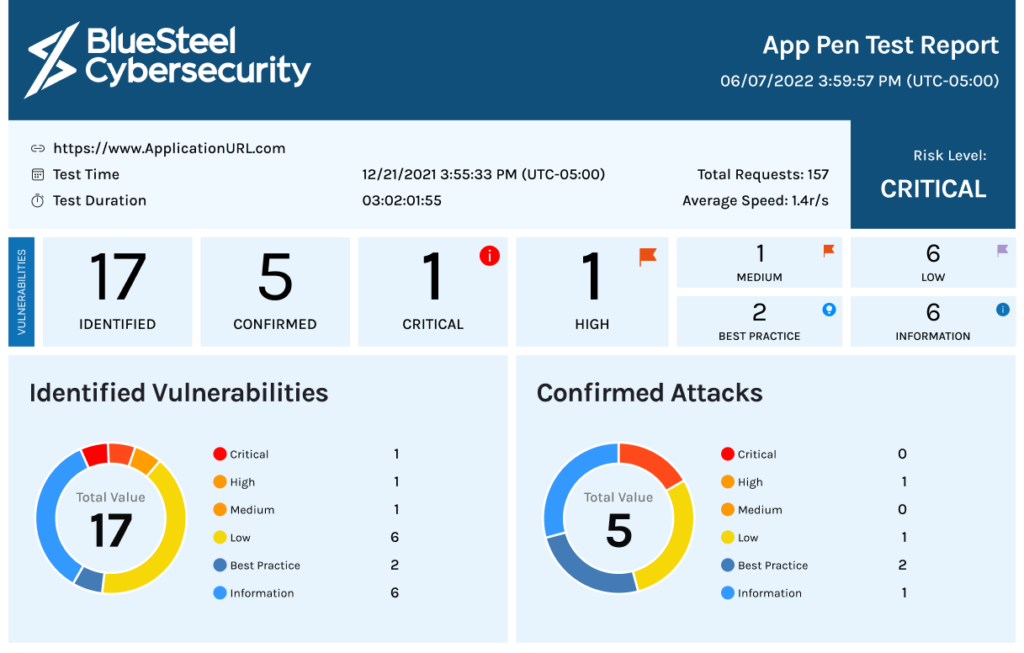
Penetration testing assists organizations in identifying and addressing security vulnerabilities, the opportunity to address these vulnerabilities, and providing a Penetration Testing Report to validate your organization’s security posture to customers.
Types of Penetration Testing and Methods
There are many types of Penetration Testing. Here are the most common:

Network Penetration Testing
This type of testing involves assessing the security of network infrastructure, including routers, switches, firewalls, and other network devices. The goal is to identify vulnerabilities that could be exploited to gain unauthorized access to the network.

Application or Software Penetration Testing
This focuses on identifying vulnerabilities in applications such as online banking systems, e-commerce websites, SaaS products, and web portals. Common vulnerabilities include SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms.

Cloud Penetration Testing
With the increasing adoption of cloud services, testing the security of cloud infrastructure and applications has become crucial. This includes assessing configurations, access controls, and data protection measures in cloud environments.

Wireless Network Penetration Testing
Wireless networks, including Wi-Fi, Bluetooth, and other wireless technologies, are tested for security weaknesses such as weak encryption, default configurations, and rogue access points.

Social Engineering
Social engineering tests the human element of security by attempting to manipulate individuals into divulging sensitive information or performing actions that compromise security. This can include phishing attacks, pretexting, and physical security breaches.

Physical Penetration Testing
This involves testing physical security measures such as locks, alarms, and access control systems. Testers attempt to gain unauthorized access to buildings or sensitive areas through methods such as lock picking, tailgating, or bypassing security checkpoints.

Red Team vs. Blue Team Exercises
Red team exercises involve simulating real-world cyberattacks to test an organization’s defenses, while blue team exercises focus on detecting and responding to these attacks. These exercises can help organizations improve their incident response capabilities and overall security posture.

Mobile Application Penetration Testing
With the proliferation of mobile devices and applications, testing the security of mobile apps is essential. This involves identifying vulnerabilities that could be exploited to compromise the confidentiality, integrity, or availability of sensitive data stored or processed by mobile applications.

Black Box Testing
In black box testing, the tester has no prior knowledge of the system being tested. This simulates the perspective of an external attacker and helps identify vulnerabilities that may not be obvious to insiders.

White Box Testing
In white box testing, the tester has full knowledge of the system’s internals, including source code, architecture, and configurations. This allows for a more comprehensive assessment of security vulnerabilities.

Gray Box Testing
Gray box testing combines elements of both black box and white box testing. Testers have partial knowledge of the system, such as limited access to source code or documentation.
PENETRATION TESTING PROCESS

What is a Penetration Test
Define the scope of the penetration test

Enumeration
Actively explore the target environment to identify live hosts, open ports, and running services.

Vulnerability Analysis:
Identify and assess potential vulnerabilities in the target systems and applications.

Exploitation
Attempt to exploit the identified vulnerabilities to gain unauthorized access or escalate privileges within the target environment.

Exploitation:
Attempt to exploit the identified vulnerabilities to gain unauthorized access or escalate privileges within the target environment.

Reporting
Document the findings of the penetration test in a comprehensive report.

Remediation and Follow-up:
Provide guidance and support to improve the overall security posture of the organization based on the findings of the penetration test.
Penetration Test Checklist

Why a Penetration Test Is Needed
There are many types of Penetration Testing. Here are the most common:

Revenue
Sales contracts typically involve an annual third-party evaluation. If you don’t have one, you may not be able to complete the transaction.

Costs
Attacks are more expensive than proactively discovering and correcting vulnerabilities before they occur. Recovering from such occurrences can be costly, including legal expenditures, regulatory fines, and reputational damage.

Continuity
Avoiding downtime and associated costs helps businesses sustain productivity and revenue streams.
What Are The Benefits of Penetration Test
Penetration testing, also known as pen testing or ethical hacking, offers several benefits to organizations:
Identifying Vulnerabilities
Penetration testing helps in identifying vulnerabilities in systems, networks, and applications before attackers can exploit them. This proactive approach allows organizations to address weaknesses before they can be exploited by malicious actors.
Enhancing Security Posture
By uncovering vulnerabilities, organizations can take steps to remediate them, thus improving their overall security posture. This can include patching software, updating configurations, or implementing additional security controls.
Risk Mitigation
Penetration testing helps in assessing and mitigating risks associated with potential security breaches. By identifying and addressing vulnerabilities, organizations can reduce the likelihood and impact of security incidents.
Compliance Requirements
Many regulatory standards and frameworks require organizations to perform penetration testing as part of their security practices. By conducting regular pen tests, organizations can demonstrate compliance with these requirements.
Awareness and Training
Penetration testing can raise awareness among employees about the importance of security best practices and the potential consequences of security breaches. It can also provide valuable training opportunities for IT and security teams to improve their skills and knowledge.
Protection of Reputation and Customer Trust
By proactively identifying and addressing vulnerabilities, organizations can protect their reputation and maintain the trust of their customers and stakeholders. Security breaches can lead to significant financial and reputational damage, so preventing them through penetration testing is crucial.
Cost Savings
While penetration testing incurs upfront costs, it can ultimately save organizations money by preventing costly security breaches. Investing in proactive security measures through pen testing can help avoid the potentially devastating financial impact of a successful cyberattack.
Continuous Improvement
Penetration testing is not a one-time activity; it should be performed regularly to keep up with evolving threats and changes in the IT environment. By incorporating pen testing into their security practices, organizations can continuously improve their security defenses and stay ahead of emerging threats.
Risk Mitigation
Penetration testing helps in assessing and mitigating risks associated with potential security breaches. By identifying and addressing vulnerabilities, organizations can reduce the likelihood and impact of security incidents.
Compliance Requirements
Many regulatory standards and frameworks require organizations to perform penetration testing as part of their security practices. By conducting regular pen tests, organizations can demonstrate compliance with these requirements.
Awareness and Training
Penetration testing can raise awareness among employees about the importance of security best practices and the potential consequences of security breaches. It can also provide valuable training opportunities for IT and security teams to improve their skills and knowledge.
Protection of Reputation and Customer Trust
By proactively identifying and addressing vulnerabilities, organizations can protect their reputation and maintain the trust of their customers and stakeholders. Security breaches can lead to significant financial and reputational damage, so preventing them through penetration testing is crucial.
Cost Savings
While penetration testing incurs upfront costs, it can ultimately save organizations money by preventing costly security breaches. Investing in proactive security measures through pen testing can help avoid the potentially devastating financial impact of a successful cyberattack.
Continuous Improvement
Penetration testing is not a one-time activity; it should be performed regularly to keep up with evolving threats and changes in the IT environment. By incorporating pen testing into their security practices, organizations can continuously improve their security defenses and stay ahead of emerging threats.
What does a Penetration Test Cost
The cost of a penetration test can vary significantly based on several factors, including the scope of the test, the complexity of the systems being tested, the depth of the assessment, the experience and reputation of the security firm or individual conducting the test, and the geographic location. Here are some general considerations that can influence the cost:

Scope
The broader the scope of the penetration test (e.g., testing multiple systems, networks, applications), the higher the cost.

Complexity
Highly complex systems or networks typically require more time and expertise to assess thoroughly, which can increase the cost.

Depth of Assessment
A basic vulnerability scan may be less expensive than a comprehensive penetration test that includes manual testing, social engineering, and advanced exploitation techniques.

Experience and Reputation
Security firms or individuals with a strong track record and reputation for delivering high-quality penetration testing services may charge more for their expertise.

Geographic Location
The cost of penetration testing can vary based on the cost of living and business operating expenses in different regions.

Regulatory Requirements
Some industries or regions have specific compliance requirements that may necessitate more extensive testing, which can impact the cost.

Frequency
Regular or ongoing penetration testing engagements may be subject to discounts compared to one-time assessments.

Additional Services:
Some firms offer additional services such as post-assessment support, training, or remediation assistance, which can increase the overall cost.
It’s essential to obtain quotes from several reputable security firms or professionals and carefully evaluate their proposals to ensure they meet your specific needs and budget constraints. Additionally, consider the long-term value of investing in thorough security testing to protect your organization from potential data breaches and cyberattacks.







