
Bridging the Gap: What HR Needs from IT and What IT Needs from HR
Introduction The digital transformation of businesses has blurred the traditional boundaries between HR and IT. Human Resources (HR) departments increasingly
NIST 800-53 is a cybersecurity compliance framework created by the National Institute of Standards in Technology (NIST).
Do you need help understanding this framework, to whom it applies, why it matters, or how to comply with it? Find some of the most essential details about NIST 800-53 below.

We manage all areas of NIST 800-53 compliance as your outsourced cybersecurity department so you don’t have to.
Our NIST 800-53 Security Program includes everything you need to meet NIST 800-53’s criteria items. This includes the following:
The NIST 800-53 guidelines were created to provide a foundation to support an organization’s cybersecurity needs. It allows for improved communication and ensures an organization’s members are on the same page.
The framework is agnostic and does not include specific recommendations for tools, companies, vendors, etc. It can easily be adapted as new tools, technologies, and systems come on the scene, too.

Provide a comprehensive and flexible catalog of controls that allow for current and future protection.

Develop a foundation for accurate technique assessment, as well as processes to determine the effectiveness of security controls.

Improve communication across organizations by providing a common lexicon to discuss risk management concepts.
From 2013 to September 2020, version four of NIST 800-53 was the most up-to-date interpretation of the guidelines. Version five included some small but significant changes, including the following:

Terminology changes: The terms “federal” and “information” were eliminated, allowing the framework to apply to all businesses and system types.

Increased privacy emphasis: Likely due to the recent increase in privacy protection laws, the fifth version includes a greater emphasis on security controls and an in-depth set for all organizations that follow NIST 800-53.

Increased operational flexibility: The newest version is less prescriptive regarding specific tools and technologies. For example, there is no set requirement for password length or complexity, but the framework still mandates complex and effective passwords.
NIST 800-53 is a set of compliance standards that all federal information systems and agencies, as well as the government contractors and departments that work with these agencies.
Compliance ensures maximum security for federal organizations, as well as the third-party businesses that work with them and process sensitive information.
It’s important to note that all organizations can adopt the NIST 800-53 framework. Because of its flexibility and comprehensiveness, it can apply to many different industries in numerous situations, whether an organization needs significant security upgrades or simply wants to build upon existing protocols.
One of the primary benefits of NIST 800-53 is that the framework is extensive and, even if followed according to the minimum controls, organizations can feel confident that they’re covering most risk factors they might encounter.
NIST 800-53 compliance also provides a solid cybersecurity baseline that organizations can improve on with time.
As breaches and the threat of breaches become more common, it is more critical than ever that organizations — especially those that work with sensitive government information — take steps to prevent issues rather than waiting until something goes wrong.
In addition to security-related benefits, compliance with NIST 800-53 offers other advantages to organizations of all types and sizes, including the following:

Save time and money by avoiding security breaches and the additional stress, work, and funds required to resolve them

Increase credibility by demonstrating a commitment to the latest cybersecurity guidelines

Increase your chances of winning new contracts because of your dedication to data security
Complying with NIST 800-53 can also help your organization improve compliance with other programs and regulations, including these:










The NIST 800-53 framework is unique because it provides a variety of controls and guidelines across several security and access control families. Each family is defined according to its baseline impact:

Losses would have catastrophic impacts

Losses would have seriously adverse impacts

Losses would have minimal negative impacts
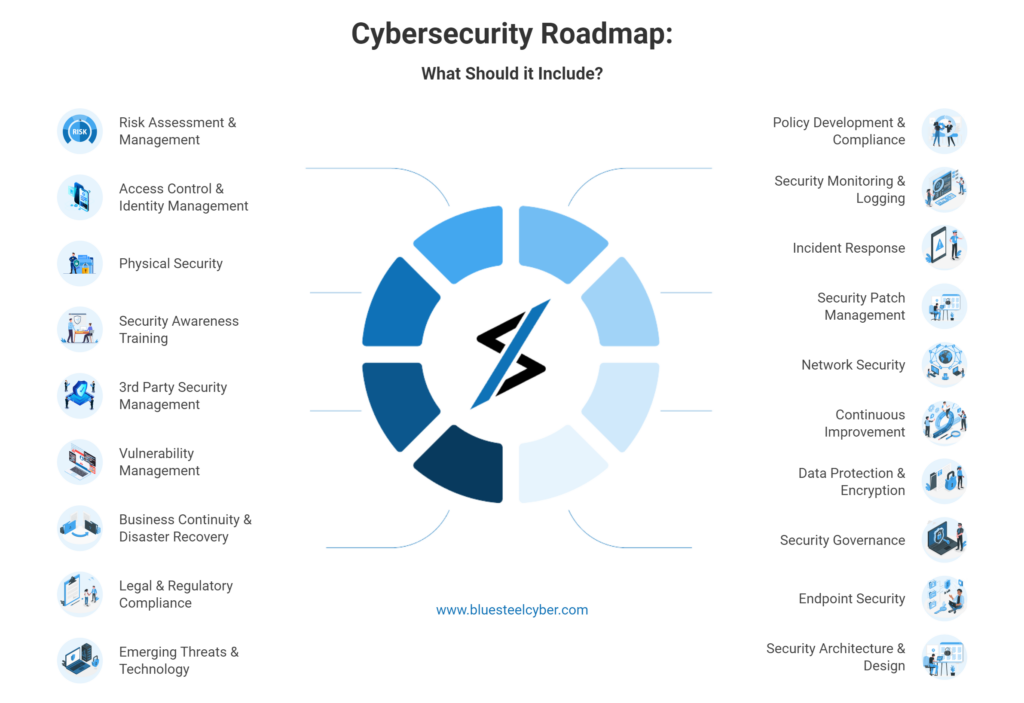
These controls are also assigned across 20 different security and control families, including the following:

Focuses on account management and monitoring, separation of duties, and enforcing the policy of least privilege principle.

Focuses on providing employees with awareness and security training, as well as elevated technical training for users with additional privileges.

Focuses on auditing records and content, records retention, and associated analysis and reporting

Focuses on penetration testing, as well as monitoring connections to public networks and external systems
Focuses on implementing configuration change controls and setting up authorized software policies

Focuses on establishing and testing business continuity strategies and alternate processing and storage sides.

Focuses on managing credentials and setting up authentication policies and systems for users, devices, and services.

Focuses on obtaining consent and authorizing privacy policies and practices.

Focuses on providing incident response training and establishing associated monitoring and reporting systems.

Focuses on implementing ongoing system, personnel, and tool maintenance.

Focuses on securing and protecting media access, use, storage, and transportation.

Focuses on establishing policies for collecting, using, and sharing personally identifiable information (or PII)

Focuses on ensuring access to emergency power, as well as securing physical access and shielding against physical risks or damage.

Focuses on defining strategies for risk management, insider threats, and scaling architecture.

Focuses on implementing strategies for comprehensive security architecture

Focuses on screening internal and external personnel and establishing termination and transfer security policies.

Focuses on identifying vulnerabilities and having ongoing privacy impact and risk assessments.

Focuses on implementing security across the system development lifecycle, as well as new vendor contracts and acquisitions.

Focuses on securing passwords and other sensitive data, partitioning applications, and implementing cryptographic key management.

Focuses on executing system monitoring, alerting systems, and remediating flaws.
Adherence to NIST 800-53 guidelines is critical to federal agencies and third-party organizations that work with those agencies. The following tips can help businesses like yours ensure compliance:
Start by figuring out the kind of data your organization deals with, as well as where you store it, how you receive it, and how you maintain and transmit it. Remember that it’s common for sensitive data to be spread across a variety of systems and applications, so it’s vital that you look carefully to get a complete picture.
Next, you must categorize and label all your sensitive data according to its unique value and sensitivity. Assign each type of information an impact value (e.g., low, moderate, or high) according to each of these security objectives: confidentiality, integrity, or availability).
A thorough risk assessment will provide you with a better understanding of where your organization currently stands and where there’s room for improvement.
At a minimum, the risk assessment should include risk identification, an assessment of the probability that these risks will occur, and the potential impact these issues could cause if they occur.
Once you understand all of these details, you can begin taking steps to remediate the most significant risks.
Your next step is to select security controls based on the specific needs and goals of your organization.
Make sure the extent of your security control selection process is proportional to the impact level of the risks you want to mitigate. Document your plan carefully and include the rationale for each control and policy you’ve chosen and implemented.
All of your employees should receive training regarding system access and cybersecurity best practices, including how to identify and report malware and other security risks. Make sure this training is an ongoing process and ensure employees have easy access to support and resources to help them make informed and proportional decisions.
Compliance with any cybersecurity framework, including NIST 800-53, is an ongoing process. It requires a continuous commitment to maintain and improve your organization’s security protocols with regular audits, especially after any security incidents occur.
Be sure to schedule regular reviews and training sessions so all employees keep cybersecurity at the top of their minds and stay committed to it long-term.

It doesn’t matter if you’re looking to overhaul your entire cybersecurity protocol or want to make some updates that keep you current with the latest safety and security regulations.
Either way, NIST 800-53 compliance can help you check the necessary boxes, add credibility to your organization, and experience peace of mind knowing your data (and your client’s data) is secure.
The guidelines and information shared above can help you comply with all tenets of NIST 800-53.
If you need more assistance achieving and maintaining compliance, Bluesteel Cybersecurity is here for you. Contact us today to learn about our compliance preparation services.

Introduction The digital transformation of businesses has blurred the traditional boundaries between HR and IT. Human Resources (HR) departments increasingly

Introduction In today’s fast-paced software development landscape, third-party code plays a crucial role in accelerating innovation and delivering value to

Introduction In critical infrastructure sectors like energy, manufacturing, and transportation, Operational Technology (OT) security is essential for protecting industrial control
Reach us Monday through Friday
8am – 6pm